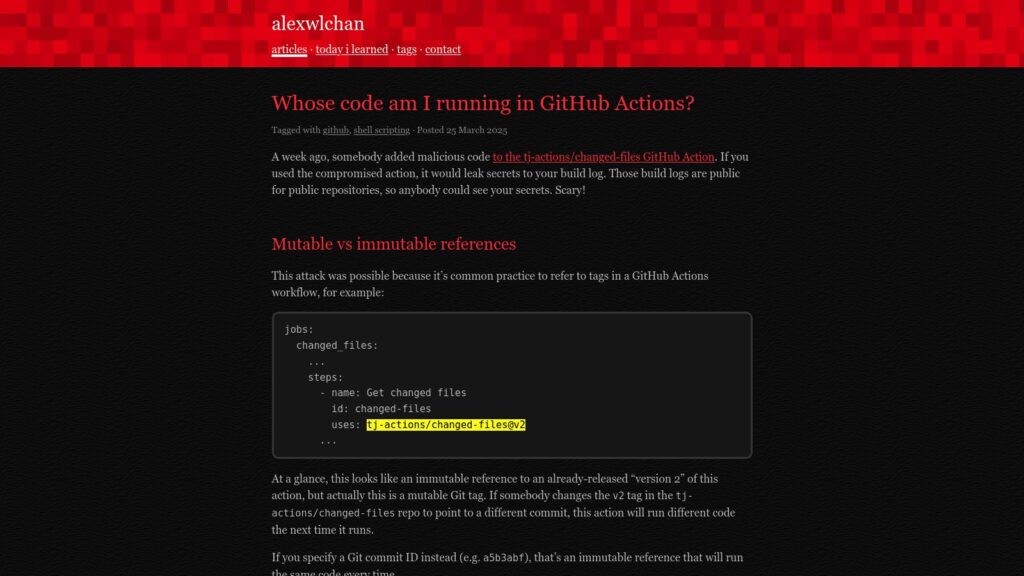
Malicious code was added to the tj-actions/changed-files GitHub Action, leaking secrets in public repositories. Using mutable Git tags can lead to unexpected code execution; using commit IDs ensures immutability. The author ran a shell script to check their GitHub Actions for such vulnerabilities and reviewed the trustworthiness of the actions based on their sources. The process involved using Unix text processing tools to extract and tally actions from workflow files, emphasizing security practices in leveraging third-party actions.
Whose Code Am I Running in GitHub Actions?